In this guide, Three methods for setting passwords are explained;
- Using the passwd command
- Using openssl
- Using the crypt function in a C program
passwd
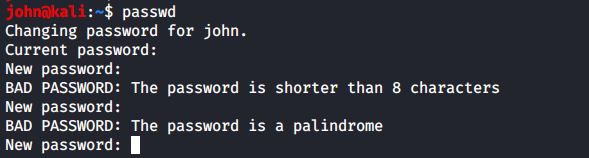
Passwords of users can be set with the passwd command. Users will have to provide their old password before twice entering the new one.
As you can see, the passwd tool will do some basic verification to prevent users from using too simple passwords. The root user does not have to follow these rules (there will be a warning though). The root user also does not have to provide the old password before entering the new password twice.
encryption with passwd
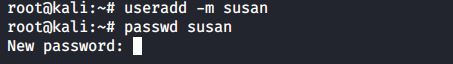
Passwords are stored in an encrypted format. This encryption is done by the crypt function. The easiest (and recommended) way to add a user with a password to the system is to add the user with the useradd -m user command, and then set the user’s password with passwd.
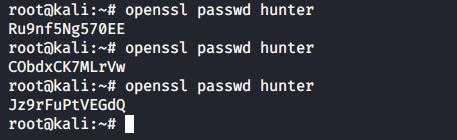
encryption with openssl
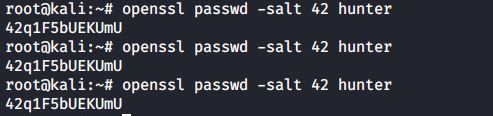
Another way to create users with a password is to use the -p option of useradd, but that option requires an encrypted password. You can generate this encrypted password with the openssl passwd command. The openssl passwd command will generate several distinct hashes for the same password, for this it uses a salt.
This salt can be chosen and is visible as the first two characters of the hash.
encryption with crypt
A third option is to create your own C program using the crypt function, and compile this into a command.
#include <stdio.h>
#define __USE_XOPEN
#include <unistd.h>
int main(int argc, char** argv)
{
if(argc==3)
{
printf("%s\n", crypt(argv[1],argv[2]));
}
else
{
printf("Usage: MyCrypt $password $salt\n" );
}
return 0;
}This little program can be compiled with gcc like this.
#gcc MyCrypt.c -o MyCrypt -lcrypt
To use it, we need to give two parameters to MyCrypt. The first is the unencrypted password, the second is the salt. The salt is used to perturb the encryption algorithm in one of 4096 different ways. This variation prevents two users with the same password from having the same entry in /etc/shadow.
# ./MyCrypt hunter2 42
Now we have learned how to secure the passwords in our Linux system. You can check this article for more password management tips.
Latest posts by Ruwantha Nissanka (see all)
- 4 ways to hide your identity using linux - January 18, 2021
- How To Install Kali Linux in Virtualbox - December 31, 2020
- Kali Linux : The OS That Hackers Use - December 31, 2020
- How to monitor user activity in Linux with Acct - December 30, 2020
- Debsecan : You will not miss another security update - December 28, 2020