In our previous post, we have discussed about how to set the standard file permissions in our linux system. In this guide we will see how to set more advanced permissions to our files.
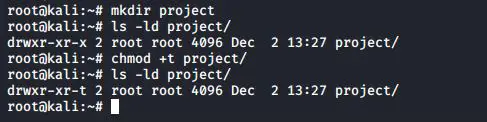
sticky bit on directory
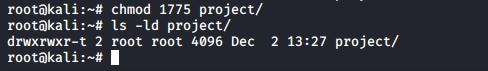
You can set the sticky bit on a directory to prevent users from removing files that they do not own as a user owner. The sticky bit is displayed at the same location as the x permission for others. The sticky bit is represented by a t (meaning x is also there) or a T (when there is no x for others).
The sticky bit can also be set with octal permissions, it is binary 1 in the first of four triplets.
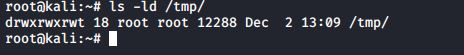
You will typically find the sticky bit on the /tmp directory.
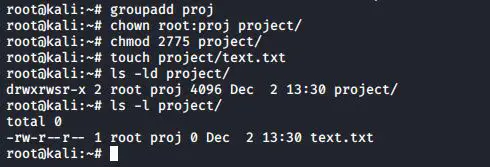
setgid bit on directory
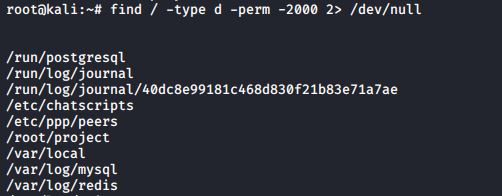
setgid can be used on directories to make sure that all files inside the directory are owned by the group owner of the directory. The setgid bit is displayed at the same location as the x permission for group owner. The setgid bit is represented by an s (meaning x is also there) or a S (when there is no x for the group owner). As this example shows, even though root does not belong to the group proj55, the files created by root in /project55 will belong to proj55 since the setgid is set.
You can use the find command to find all setgid directories.
setgid and setuid on regular files
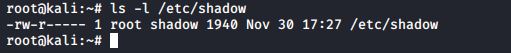
These two permissions cause an executable file to be executed with the permissions of the file owner instead of the executing owner. This means that if any user executes a program that belongs to the root user, and the setuid bit is set on that program, then the program runs as root. This can be dangerous, but sometimes this is good for security. Take the example of passwords; they are stored in /etc/shadow which is only readable by root. (The root user never needs permissions anyway.)
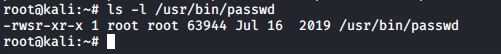
Changing your password requires an update of this file, so how can normal non-root users do this? Let’s take a look at the permissions on the /usr/bin/passwd.
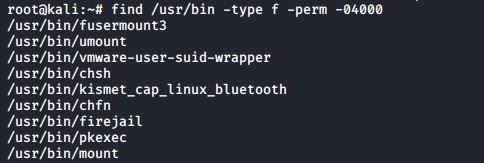
When running the passwd program, you are executing it with root credentials. You can use the find command to find all setuid programs.
In most cases, setting the setuid bit on executables is sufficient. Setting the setgid bit will result in these programs to run with the credentials of their group owner.
Latest posts by Ruwantha Nissanka (see all)
- 4 ways to hide your identity using linux - January 18, 2021
- How To Install Kali Linux in Virtualbox - December 31, 2020
- Kali Linux : The OS That Hackers Use - December 31, 2020
- How to monitor user activity in Linux with Acct - December 30, 2020
- Debsecan : You will not miss another security update - December 28, 2020