The following are two reasons why you would want to keep track of what network services are running on your system:
- To ensure that no legitimate network services that you don’t need are running
- To ensure that you don’t have any malware that’s listening for network connections from its master
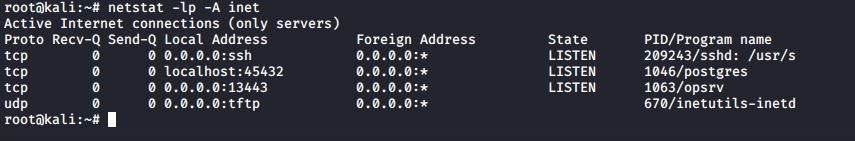
You can use the following command to see a list of network services that are listening
#netstat -lp -A inet
Here’s the breakdown:
- -lp: The l means that we want to see which network ports are listening. In other words, we want to see which network ports are waiting for someone to connect to them. The p means that we want to see the name and process ID number of the program or service that is listening on each port.
- -A inet: This means that we only want to see information about the network protocols that are members of the inet family. In other words, we want to see information about the raw, tcp, and udp network sockets, but we don’t want to see anything about the Unix sockets that only deal with interprocess communications within the operating system.
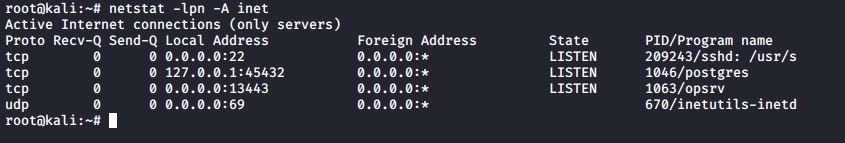
If you want to see port numbers and IP addresses instead of network names, add the n option
#netstat -lpn -A inet
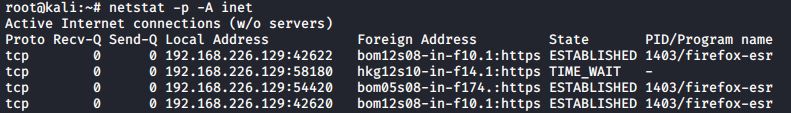
to view the established TCP connections, leave out the l option.
#netstat -p -A inet
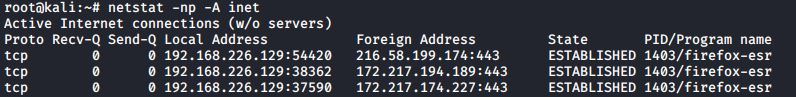
The Foreign Address column shows the address and port number of the machine at the remote end of the connection. Because the names of those foreign addresses don’t make much sense, let’s add the n option to see the IP addresses instead:
#netstat -np -A inet
Something to keep in mind is that rootkits can replace legitimate Linux utilities with their own trojan versions. For example, a rootkit could have its own trojan version of netstat that would show all network processes except for those that are associated with the rootkit. That’s why you want something such as Rootkit Hunter in your toolbox.
Latest posts by Ruwantha Nissanka (see all)
- 4 ways to hide your identity using linux - January 18, 2021
- How To Install Kali Linux in Virtualbox - December 31, 2020
- Kali Linux : The OS That Hackers Use - December 31, 2020
- How to monitor user activity in Linux with Acct - December 30, 2020
- Debsecan : You will not miss another security update - December 28, 2020