You may work for a super-secret government agency, or you may be just a regular citizen. Either way, you still have sensitive data in your linux system that you need to protect from prying eyes. For that, we can use GNU Privacy Guard to encrypt or cryptographically sign files or messages in our linux machine. GPG uses strong, hard-to-crack encryption algorithms and You can use GPG to just encrypt your own files for your own use
Create your pair of GPG keys
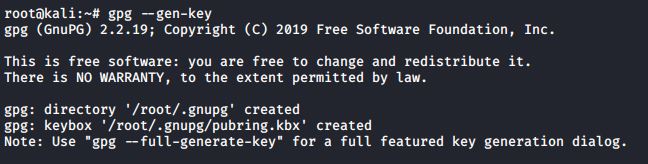
The first thing you need to know is how to create your GPG keys.
#gpg --gen-key
The first thing that this command does is to create a populated .gnupg directory in your home directory:
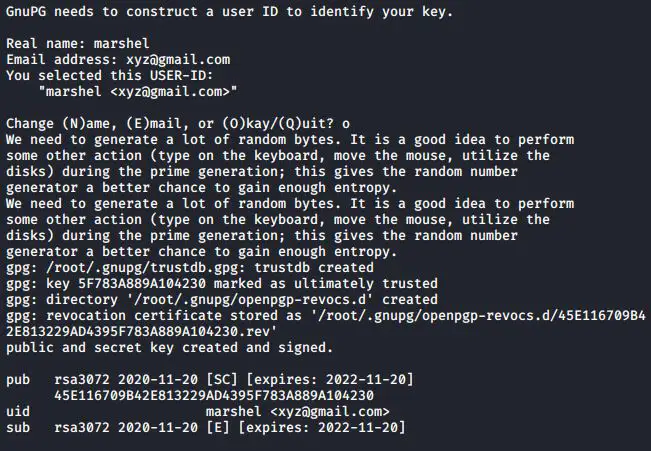
You’ll then be asked to provide your personal information:
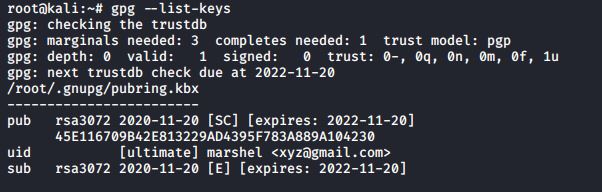
Verify that the keys did get created:
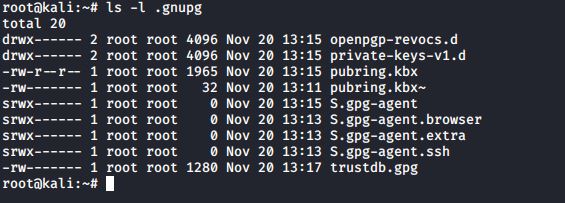
While you’re at it, take a look at the files that you created:
These files are your public and private keyrings, your own gpg.conf file, a random seed file, and a trusted users database.
Symmetrically encrypting your own files
You may find GPG useful for encrypting your own files, even when you never plan to share them with anyone else. For this, you’ll use symmetric encryption, which involves using your own private key for encryption.
Create a file using the following command
#touch secret.txt
Encrypt it using the following command
#gpg -c secret.txt
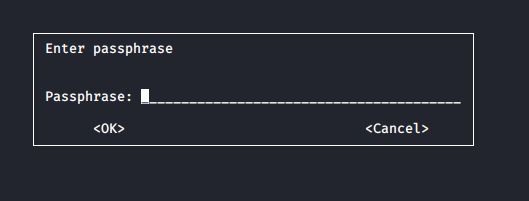
You will be prompted to create a passphrase for the file
Note that the -c option indicates that I chose to use symmetric encryption with a passphrase for the file. The passphrase that you enter will be for the file, not for your private key.
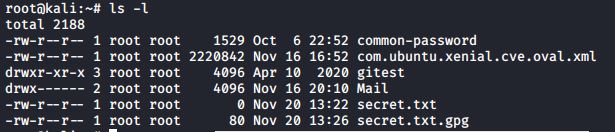
Look at your new set of files. One slight flaw with this is that GPG makes an encrypted copy of the file, but it also leaves the original, unencrypted file intact:
Remove the unencrypted file using the -u option to delete the file, and the -z option to overwrite the deleted file with zeros:
#shred -u -z secret_squirrel_stuff.txt
Now you can open the encrypted file using the following command and the passphrase
#less secret.txt
Latest posts by Ruwantha Nissanka (see all)
- 4 ways to hide your identity using linux - January 18, 2021
- How To Install Kali Linux in Virtualbox - December 31, 2020
- Kali Linux : The OS That Hackers Use - December 31, 2020
- How to monitor user activity in Linux with Acct - December 30, 2020
- Debsecan : You will not miss another security update - December 28, 2020