Welcome to our brand-new tutorial series on Linux security hardening. In this tutorial series, we will cover security and hardening techniques that apply to any Linux based server or workstation. By following this guide, you can make sure that no attacker can compromise your Linux system. This guide will contain a total of 7 sections as shown below.
- Disabling root access and setting up sudo privileges for full administrative users
- Securing your server with a firewall
- Encrypting and SSH hardening
- Mastering discretionary access control
- Access control lists and shared directory management
- Implementing mandatory access control with SELinux and app armour
- Scanning, auditing and hardening
This tutorial series will be a basic-to-advanced level guide filled with real-world examples that will help you secure your Linux system. by the end of this series, you will be equipped with many tools at your disposal which will help you to fully protect your system.
So, Let’s start.
Section 1: Disabling root account and setting up sudo privileges for full administrative users
The user “root” is the default administration account on Linux and other Unix operating systems. Since this account has superuser access with permissions to read, write and execute all files and commands, it is necessary to disable this user and setup superuser privileges to another admin user.
- Make sure to create an administrative account before disabling root. We will create a user called “AdminUser” for this.
# useradd -m -c “AdminUser” admin
# passwd admin
- Add the user “AdminUser” to sudo group
# usermod -aG sudo admin
Now, the user “AdminUser” can be used for administrative tasks instead of using “root”.
- Switch to the “AdminUser”
# su admin
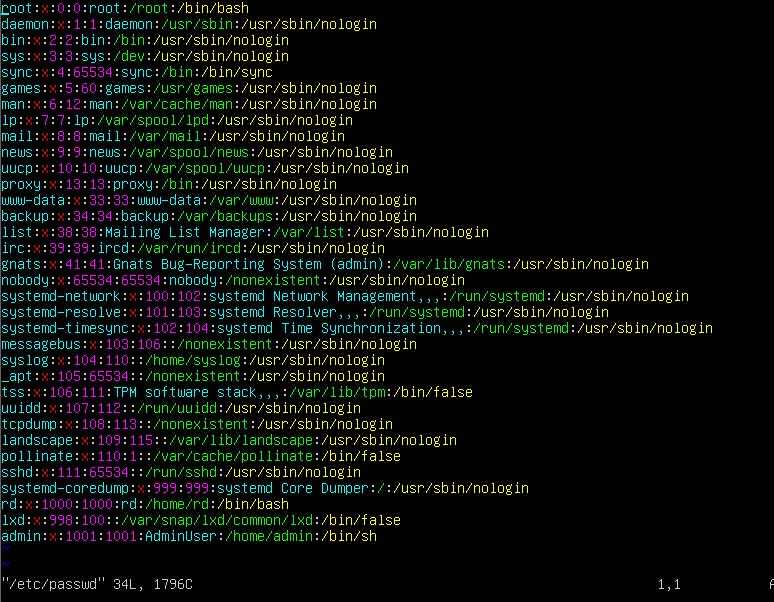
- Now disable root user shell so that he cannot login. To do that, edit /etc/passwd file as shown below
# vim /etc/passwd
- Change the root user shell from /bin/bash to /sbin/nologin
- Save this file and close it
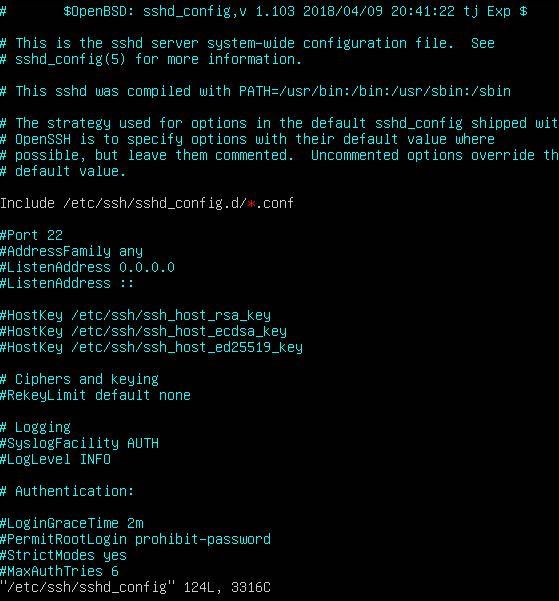
- To Disable root login via SSH, go to /etc/ssh/sshd_config file
# sudo vim /etc/ssh/sshd_config
- set the PermitRootLogin value to no
- Save and exit
From now on, root account cannot be used to login to this Linux machine with administrative privileges. In our next tutorial, we will see how to Secure your Linux machine with a firewall.
Stay tuned…
Latest posts by Ruwantha Nissanka (see all)
- 4 ways to hide your identity using linux - January 18, 2021
- How To Install Kali Linux in Virtualbox - December 31, 2020
- Kali Linux : The OS That Hackers Use - December 31, 2020
- How to monitor user activity in Linux with Acct - December 30, 2020
- Debsecan : You will not miss another security update - December 28, 2020