Netcat (also known as ‘nc’) is a networking tool used for reading or writing from TCP and UDP sockets using an easy interface. It is designed as a dependable ‘back-end’ device that can be used directly or easily driven by other programs and scripts. Therefore, this tool is a treat to network administrators, programmers, and pen-testers as it’s a feature rich network debugging and investigation tool.
To open netcat simply go to your shell and enter ‘nc’:
#nc
Connecting to a host with Netcat
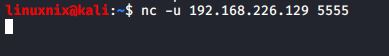
Use the -u option to start a TCP connection to a specified host and port:
#nc -u <host_ip> <port>
Listen to inbound connections
You can set nc to listen on a port using -l option
#nc -l <port>
Scan ports with Netcat
This can easily be done using the ‘-z’ flag which instructs netcat not to initiate a connection but just check if the port is open. For example, In the following command we instruct netcat to check which ports are open between 80 and 100 on ‘localhost‘
#nc -z <host_ip> <port_range>
Advanced port scan
To run an advanced port scan on a target, use the following command
#nc -v -n -z -w1 -r <target_ip>
This command will attempt to connect to random ports (-r) on the target ip running verbosely (-v) without resolving names (-n). without sending any data (-z) and waiting no more than 1 second for a connection to occur (-w1)
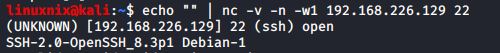
TCP banner grabbing With Netcat
You can grab the banner of any tcp service running on an ip address using nc:
#echo “” | nc -v -n -w1 <target_ip> <port_range>
Transfer Files with Netcat
For this, you should have nc installed on both sending and receiving machines. First you have to start the nc in listener mode in receiving host
#nc -l <port> > file.txt
Now run the following command on the sending host:
#nc <target_ip> <port> --send-only < data.txt
In conclusion, Netcat comes with a lot of cool features that we can use to simplify our day-to-day tasks. Make sure to check out this article to learn some more interesting features in this tool.
Latest posts by Ruwantha Nissanka (see all)
- 4 ways to hide your identity using linux - January 18, 2021
- How To Install Kali Linux in Virtualbox - December 31, 2020
- Kali Linux : The OS That Hackers Use - December 31, 2020
- How to monitor user activity in Linux with Acct - December 30, 2020
- Debsecan : You will not miss another security update - December 28, 2020