So, you have a directory full of super-secret files that only a very few people need to see, and you want to know when unauthorized people try to see them. Or, maybe you want to see when a certain file gets changed, or you want to see when people log into the system and what they’re doing once they do log in. For all this and more, you have the auditd system.
Install auditd
Run the following command to install auditd
#apt install auditd
Creating audit rules
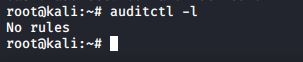
First, let’s check to see whether any audit rules are in effect:
#auditctl -l
As you can see, the auditctl command is what we use to manage audit rules. The -l option lists the rules.
Auditing a file for changes
Now, let’s say that we want to see when someone changes the /etc/passwd file.
#auditctl -w /etc/passwd -p wa -k passwd_changes
The breakdown:
-w: This stands for where, and it points to the object that we want to monitor. In this case, it’s /etc/passwd.
-p: This indicates the object’s permissions that we want to monitor. In this case, we’re monitoring to see when anyone either tries to (w)rite to the file or tries to make (a)ttribute changes. (The other two permissions that we can audit are (r)ead and e(x)ecute.)
-k: The k stands for key, which is just auditd’s way of assigning a name to a rule. So, passwd_changes is the key, or the name, of the rule that we’re creating
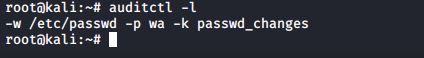
The auditctl -l command shows us that the rule is indeed there.
#auditctl -l
Saving the AuditD rule
the rule is only temporary and will disappear when we reboot the machine. To make it permanent, we need to create a custom rules file in the /etc/audit/rules.d/ directory.
You could use your text editor to create a new rules file in the /etc/audit/rules.d/ directory. Alternatively, you could just redirect the auditctl -l output into a new file, like this:
#sh -c "auditctl -l > /etc/audit/rules.d/custom.rules” #systemctl restart auditd
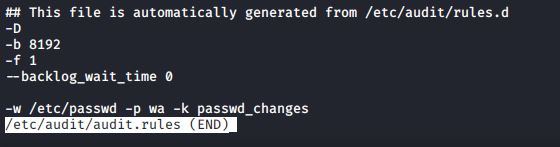
After restarting the auditd daemon, our audit.rules file now looks like this:
#less /etc/audit/audit.rules
Here’s the breakdown for this file:
-D: This will cause all rules and watches that are currently in effect to be deleted so that we can start from a clean slate.
-b 8192: This sets the number of outstanding audit buffers that we can have going at one time.
-f 1: This sets the failure mode for critical errors, and the value can be either 0, 1, or 2.
Now, the rule will take effect every time the machine is rebooted, and every time that you manually restart the auditd daemon.
Latest posts by Ruwantha Nissanka (see all)
- 4 ways to hide your identity using linux - January 18, 2021
- How To Install Kali Linux in Virtualbox - December 31, 2020
- Kali Linux : The OS That Hackers Use - December 31, 2020
- How to monitor user activity in Linux with Acct - December 30, 2020
- Debsecan : You will not miss another security update - December 28, 2020