Nikto is a special-purpose tool with only one purpose; that is, it’s meant to scan web servers, and only web servers. It’s easy to install, easy to use, and capable of doing a comprehensive scan of a web server fairly quickly.
Nikto is built on LibWhisker2 (by RFP) and can run on any platform which has a Perl environment. It supports SSL, proxies, host authentication, attack encoding and more. It can be updated automatically from the command-line, and supports the optional submission of updated version data back to the maintainers.
To install on Ubuntu, use the following command:
#apt install nikto libnet-ssleay-perl
The next thing you’ll want to do is update the database of vulnerability signatures. To update the vulnerability database, use the following command:
#nikto -update
To do a simple web server scan, use the -h option to specify the target host
#nikto -h <web_server_ip>
One of the great things you can do with nikto is to specify the type of checks it runs. So, to only perform an Denial of Service test against your target.
#nikto -tuning x 6 -h <web_server_ip>
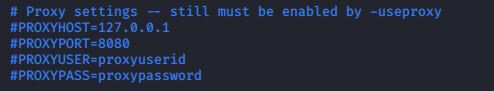
If you want to to be anonymous while scanning a particular web for vulnerabilities you can use a proxy server where It hides your IP address and other information. Edit the configuration file for nikto as follows.
#vi /etc/nikto/config.tx
Navigate to Proxy settings and change it as follows.
PROXYHOST=85.28.28.209
PROXYPORT=8080
Now you can start the scan as follows.
#nikto -useproxy -h <web_server_ip>
It might be good to enable verbose output.
#perl nikto.pl -Display V -h <web_server_ip>
check the additional options supported by nikto using the help switch as follows.
#nikto -help
You can output to a file with the -o option. You can specify the format of the output file with -Format also which is not mandatory.
- csv – Comma-separated-value
- htm – HTML Format
- msf+ – Log to Metasploit
- nbe – Nessus NBE format
- txt – Plain text (default if not specified)
- xml – XML Format
#nikto -h <web_server_ip> -o results.txt
Latest posts by Ruwantha Nissanka (see all)
- 4 ways to hide your identity using linux - January 18, 2021
- How To Install Kali Linux in Virtualbox - December 31, 2020
- Kali Linux : The OS That Hackers Use - December 31, 2020
- How to monitor user activity in Linux with Acct - December 30, 2020
- Debsecan : You will not miss another security update - December 28, 2020