As we have already discussed in one of our previous articles, ARP protocol is commonly used by layer two devices to communicate and discover each other easily. The arping utility performs an action similar to ping, but at the Ethernet layer. Where we can use ping to tests the reachability of an IP address, arping can be used to report the reachability and round-trip time of an IP address hosted on the local network.
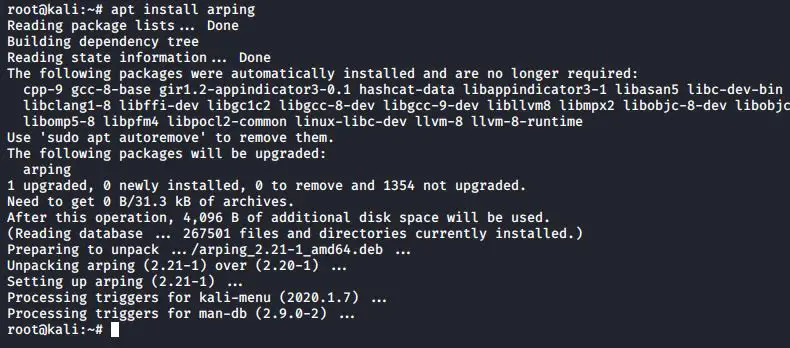
You can use the following command to install arping in yur system
#apt install arping
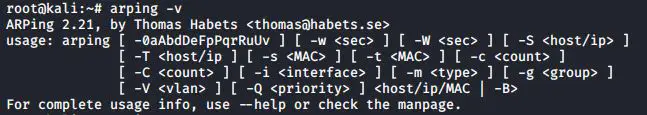
Execute the following to check the version
#arping -v
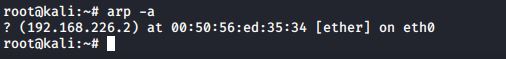
To check the current ARP entries in your ARP table, issue the following command
#arp -a
In this case, I am presented with the only entry in my ARP table : a router accessible via the 192.168.226.2 IP address.
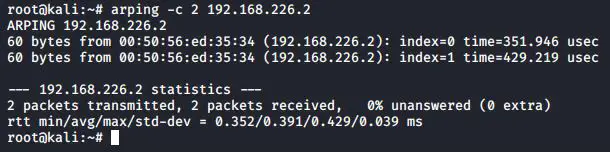
Execute the following command to ping a host using arping
#arping -c 2 <ip_address>
Here I have specified the number of pings to be sent using the “-c” option for “count”.
As you can see, if you are getting response pings, you are presented with the MAC address of the corresponding device.
You will have to specify the network interface if you have multiple network interfaces on your system. You can do it by using the following command
#arping -I <interface_name> <ip address>
You can specify the source MAC address you are sending packets from using the following command
#arping -c 2 -s <mac_address> <ip_address>
In this scenario, you can use 2 options
- You are the owner of the MAC address and you can simply use the “-s” option.
- You are not the owner of the MAC address and you are trying to spoof the MAC address. In this case, you need to use the promiscuous mode using the “-p” option
#arping -c 2 -s <mac_address> -p <ip_address>
Latest posts by Ruwantha Nissanka (see all)
- 4 ways to hide your identity using linux - January 18, 2021
- How To Install Kali Linux in Virtualbox - December 31, 2020
- Kali Linux : The OS That Hackers Use - December 31, 2020
- How to monitor user activity in Linux with Acct - December 30, 2020
- Debsecan : You will not miss another security update - December 28, 2020